10+ jwt sequence diagram
The diagram below show how our system handles User Registration and User Login processes. The user logins the account.

An Authentication Authorization Microservice With Clean Architecture Dev Community
The JwtSecurityTokenHandler class in the.

. JWT Authentication Sequence Diagram. Validate a token. Reference implementation for using JWT authorization with Hive - hive-jwt-authsequence-diagramtxt at master hivestreaminghive-jwt-auth.
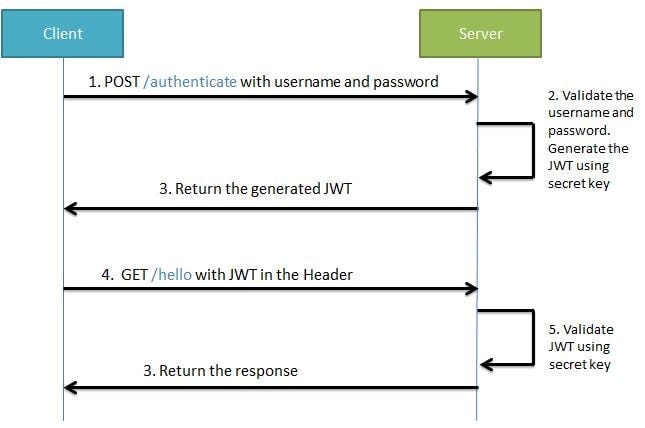
The JWT implementation is less chatty and more. Different types of tokens perishable token session token access token and refresh token that have different properties such as expiration time and reusability are described in Kubovy et. Lets understand how JWT works with a sequence diagram.
Contribute to NathanKrexpress-server-jwt development by creating an account on GitHub. You can edit this template. Im designing a JWT authentication workflow for a RESTful API which uses two kinds of tokens.
PixelHelth JWT-Authentication classic Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple image formats. You can edit this. Phone token a short-lived token - issued by completing an One-Time.
While the JWT flow to GET the authenticated user whose ID is 123 will typically look like the sequence diagram below. After you instantiate the configurationManager keep it around as a singletonYou only need to set it up once. The diagram below show how our system handles User Registration and User Login processes.
- SUGGESTED SEQUENCING WITH AUTHORISATION METHODS - participant ClientnSites as C participant IdentitynService as I participant. JWT-Authentication classic Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple image formats. JWT represents a set of claims as a.
The request flow is shown in the above sequence diagram. In summary the frontend should exchange valid user credentials for a JWT issued by the backend using the. The application requests an authentication token from the trusted third party.
Learn how to integrate your software with our application-restricted RESTful APIs - using our signed JWT authentication pattern. How Do Jwt Tokens Work. In the JWT authentication process the.
JWT claims can be digitally signed or integrity protected with a Message Authentication Code MAC and they can also be encrypted. JWT Authentication Sequence Diagram.

Saml Based User Authentication And Sso In Web Application By Sandeep Kumar Medium

An Authentication Authorization Microservice With Clean Architecture Dev Community

An Authentication Authorization Microservice With Clean Architecture Dev Community

An Authentication Authorization Microservice With Clean Architecture Dev Community

Kerberos Based User Authentication And Sso In Web Application By Sandeep Kumar Medium

Saas Noise
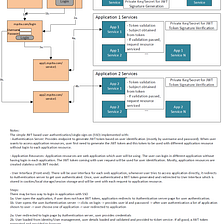
Saml Based User Authentication And Sso In Web Application By Sandeep Kumar Medium

An Authentication Authorization Microservice With Clean Architecture Dev Community
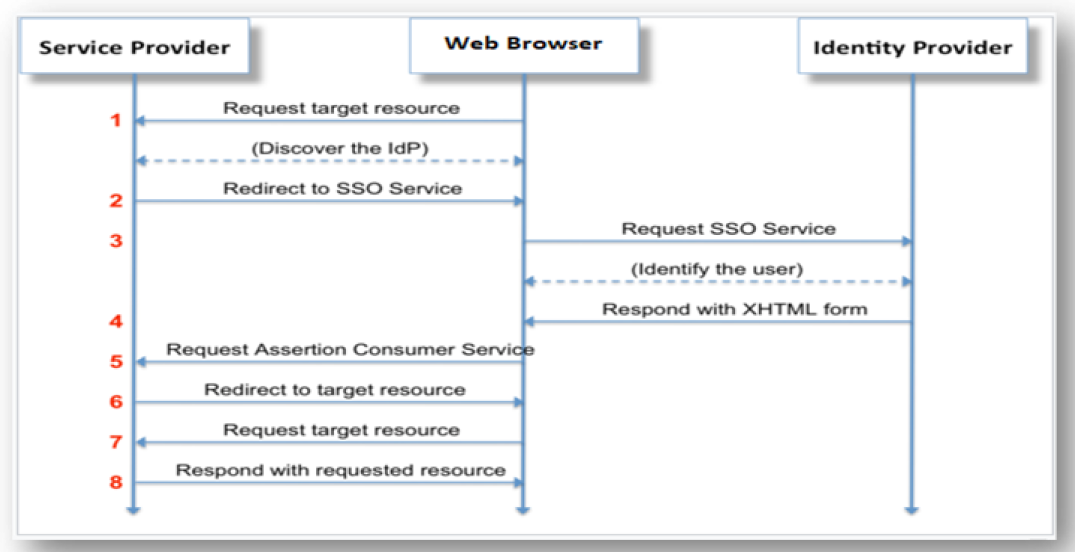
Saml Based User Authentication And Sso In Web Application By Sandeep Kumar Medium

Sysml Solution Software Development Sequence Diagram Solutions
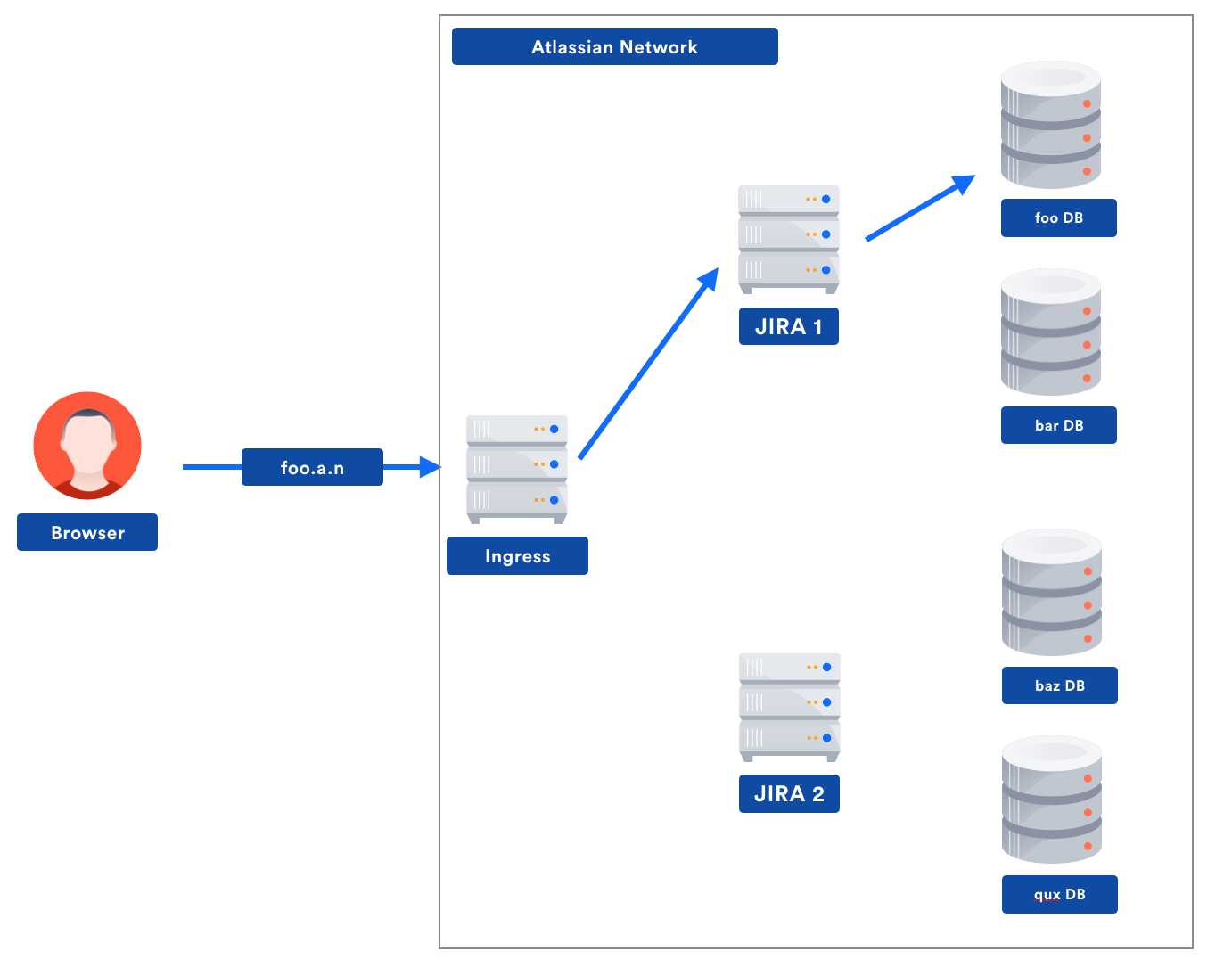
Our Not So Magic Journey Scaling Low Latency Multi Region Services On Aws Atlassian Engineering

An Authentication Authorization Microservice With Clean Architecture Dev Community

Google Open Source Blog 2017

An Authentication Authorization Microservice With Clean Architecture Dev Community
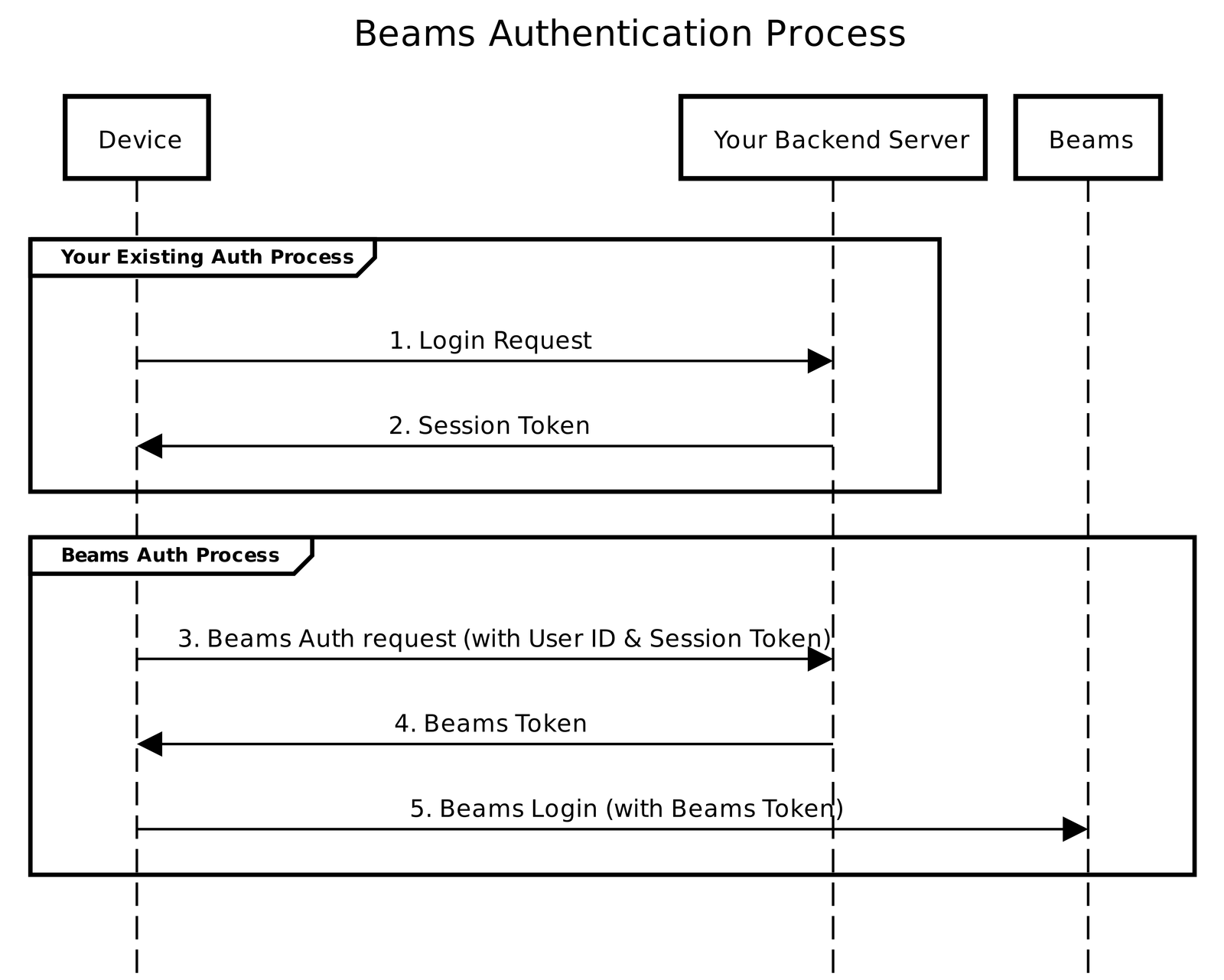
Pusher Beams Client Api Demo For Ios
React Serverless Authentication System Part 1 Netlify Function By Mir Sahib The Startup Medium

Creating A Spring Petclinic App With Jhipster Agency04